Pegasus is the hacking software – or spyware – that is developed by NSO Group, an Israeli company that is licensed to governments around the world. It has the capability to infect billions of phones running either iOS or Android operating systems and perhaps the most powerful spyware.
It made first headlines in 2019 when Facebook-owned WhatsApp confirmed that the spyware was used to target around 1,400 users including journalists and human rights activists in India. WhatsApp made this disclosure in a US law court in San Francisco.
WhatsApp claims to have fixed its software vulnerabilities that allowed Pegasus to penetrate a mobile phone just by giving the person a WhatsApp video missed call.
How Pegasus Penetrates a Phone?
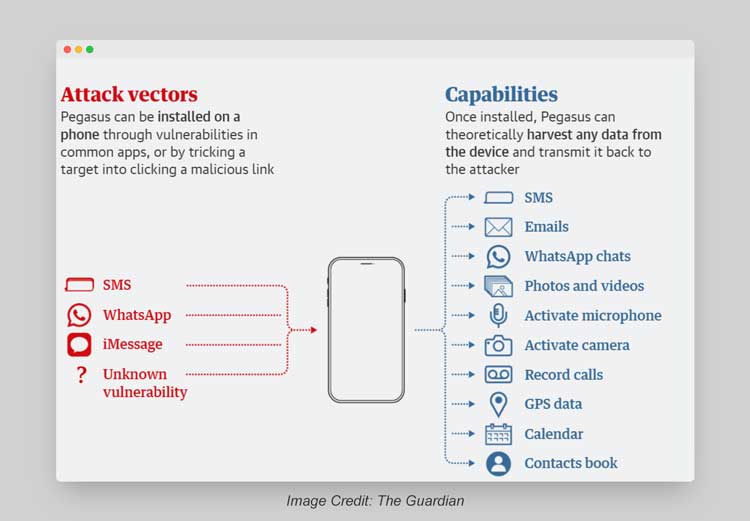
Pegasus can be installed on a phone through vulnerabilities in common apps, or by tricking a target into clicking a malicious link.
In a general way, it can infect devices that are connected to the internet. Some updated versions, experts claim, can also infect phones without the victim clicking on any links or messages.
What happens after Pegasus Penetrates your device?
Once installed, the Pegasus spyware hides from the background, where it keeps functioning continuously. The Application commonly attacks most used apps such as WhatsApp, Call, SMS, or iMessage and tries to gain “root privileges” – such that it can become the device system administrator.
The Application can automatically turn on the camera, the microphone, and the GPS. It can thus also look in the call logs and can read the encrypted chats and backup. The spyware can also get access to the SMS, Emails based on the instructions from a remote server.
The spyware hides skillfully using built-in self-destruct capabilities. If Pegasus fails to connect with its command-and-control server for more than 60 days, it self-destructs and removes all traces. If it detects that it was installed on the wrong device or sim card, it will again self-destruct.
What is Zero-Click Attack?
A worrying aspect that has been revealed is the ability of this spyware to infect a device by a ‘zero-click’ attack, which does not require any action from the mobile’s user.
Zero-click attacks are tough to identify as it is associated directly to the OS. To stay safe, users must ensure that the software and apps in the device are updated and that any app in use is directly installed from Google Play Store or Apple’s App Store. Users must also avoid clicking links in email, text or message that does not look reputable.


